Elective ICT Pasco 2020 Objectives

Elective ICT Pasco 2020 Objectives
Answer all questions
1. A report that shows out-of-the-ordinary data is called
A. confidential report
B. essential report
C. exception report
D. special report
Ans: C
2. The practice of sending unsolicited electronic mail to users of the internet is referred to as
A. hacking
B. hijacking
C. jamming
D. spamming
Ans: D
3. A computer program that combines two or more applications into single unified package is called
A. custom software
B. integrated software
C. off-the-shelf software
D. specialized software
Ans: B
4. The term What-if Analysis is associated with
A. database application
B. desktop publishing application
C. spreadsheet application
D. word processing application
Ans: C
5. Which of the following programs is an operating system?
A. Internet Explorer
B. Mozilla Firefox
C. Opera
D. Unix
Ans: D
6. The finite and ordered sequence of steps which must be taken in order to solve a given problem is known as
A. algorithm
B. compilation
C. flowcharting
D. iteration
Ans: A
7. A topology that has a central workstation from which all other nodes relate is called
A. bus
B. mesh
C. ring
D. star
Ans: D
8. In a one-to-many relationship, the table in one side and that on the many side respectively are referred to as
A. child, parent
B. parent, child
C. father, son
D. son, father
Ans: B
9. The ASCII code is used for information interchange by a binary code for
I. Alphabets;
II. Numbers;
III. Symbols;
Which of the following options is correct?
A. I and II only
B. I and III only
C. II and III only
D. I, II and III
Ans: D
10. BCD coding numbers are obtained when
A. converting decimal to octal
B. converting binary to decimal
C. converting decimal to binary
D. each decimal digit is represented by four bit binary
Ans: C
11. Which of the following options is not common between computer files and manual files? They can both
A. be accessed
B. be retrieved
C. store video
D. be arranged
Ans: C
12. False information dissemination in the broadcast of information technology assignment must have come from
A. wrong input selection
B. inadequate power supply
C. low capacity of the memory
D. invasion of the computer system by virus
Ans: A
13. Health hazards associated with the use of ICT include:
I. Repetitive-Strain Injury,
II. Carpel Tunnel Syndrome,
III. Computer Vision Syndrome,
IV. Magnetic Resonance Imaging.
Which of the following options is correct?
A. I, II and III only
B. II, III and IV only
C. I, II and IV only
D. I, III and IV only
Ans: A
14. Desktop publishing relies on hardware support such as
I. low resolution monitors,
II. high resolution scanners,
III. low resolution scanners,
IV. high resolution monitors.
Which of the following options will give the best support?
A. I and III only
B. II and III only
C. II and IV only
D. III and IV only
Ans: D
15. Which of the following statements are true about gridlines in spreadsheet?
I. Gridline may be turned off for display but turned on for printing
II. Gridline may be turned on or off for printing
III. Gridline may be turned off for display and printing
A. I and II only
B. I and III only
C. II and III only
D. I, II and III
Ans: D
16. The size of the virtual memory depends on the size of the
A. address bus
B. control bus
C. data bus
D. main memory
Ans: A
17. Which of the following memory types are examples of non-volatile memory?
I. PROM
II. SRAM
III. EEPROM
IV. DRAM
A. I and II only
B. I and III only
C. II and III only
D. III and IV only
Ans: B
18. Which of the following devices output can be measured by resolution?
I. Keyboard
II. Monitor
III. Printer
A. I and II only
B. I and III only
C. II and III only
D. I, II and III
Ans: C
19. Which of the following devices help prevent power surge?
A. Spike protector
B. Surge suppressor
C. High-grade multi-meter
D. Uninterrupted power supply
Ans: D
20. Formatting a hard disk results in all the data being
A. backup to the disk
B. copied from the disk
C. deleted from the disk
D. saved to another disk
Ans: C
21. Which of the following devices can be used to directly input printed text?
A. Joystick
B. Mouse
C. Touch pad
D. Optical Character Recognition
Ans: D
22. A set of instructions that determines how hardware and operating system will communicate with application software is referred to as
A. firmware
B. groupware
C. malware
D. testware
Ans: A
23. When the time slot given to a process in a time sharing operating system is completed, the process goes from running state to
A. blocked state
B. ready state
C. suspended state
D. terminated
Ans: B
Use figure 1 to answer question 24 to 26
24. The basic problem with the flowchart in Figure 1 is that, it has
A. no direction
B. no algorithm
C. ‘stop’ as a process
D. improper branch out
Ans: A
25. What activity is the flowchart made to represent
A. How to pick an orange
B. Instruction to pick an orange
C. Instruction not to pick an orange
D. Number of times to pick an orange
Ans: D
Also Check: Elective ICT Pasco 2018 Objectives
26. If N in the flowchart is represented by 10, which of the following conditions is not true?
A. If C > 10, do not pick orange
B. If C = 10, stop picking orange
C. If C < 10, keep picking orange
D. If C = 10, continue picking orange
Ans: D
27. Which of the following errors is not associated with computer programming?
A. Compile error
B. Grammar error
C. Logic error
D. Syntax error
Ans: B
28. Mozilla Firefox is an example of a
A. web crawler
B. web browser
C. web server
D. web site
Ans: B
29. Which of the following network topologies is most difficult to troubleshoot?
A. Bus
B. Mesh
C. Ring
D. Star
Ans: C
30. Which of the following terms will lead to communication between separate computer systems?
A. Bridging
B. Configuration
C. Connectivity
D. Routing
Ans: B
Also Read: Elective ICT Practicals 2020
Table 1, “SpareParts”, shows the data on car parts being sold by a dealer at the AbosseyOkai market. Use the table to answer questions 31 to 34.
| PartNumber | PartDescription | QuantityOnHand | WareHouseNumber | UnitPrice |
| EX214 | Exhaust Pipe | 300 | 22 | 200 |
| BA345 | Ball Bearing | 200 | 4 | 400 |
| WI671 | Wind Screen | 400 | 7 | 315 |
| MI234 | Mirror | 590 | 6 | 45 |
| SH234 | Shock | 300 | 8 | 570 |
| IN568 | injectors | 200 | 20 | 1000 |
31. The data type for the field PartNumber in the SpareParts table is
A. Currency
B. Hyperlink
C. Number
D. Text
Ans: D
32. The number of fields in the SpareParts table is
A. 4
B. 5
C. 6
D. 7
Ans: B
33. How many records are in the SpareParts table?
A. 4
B. 5
C. 6
D. 7
Ans: C
34. The primary key in the SpareParts table is
A. SpareParts.UnitPrice
B. SpareParts.PartNumber
C. SpareParts.QuantityOnhand
D. SpareParts.WareHouseNumber
Ans: B
35. ICT in education includes the following resources except
A. blog
B. internet
C. onlineform
D. computer programming
Ans: D
36. The use of information and communications technology for health care practice support is known as electronic
A. book
B. business
C. health
D. learning
Ans: C
37. A hexadecimal number A0 has the decimal value
A. 80
B. 120
C. 160
D. 254
Ans: C
38. Text composition in desktop publishing does not include
A. creating drop caps
B. embedding fonts
C. adjusting line lengths
D. adding bold and italic type
Ans: C
39. To improve the appearance of a layout in desktop publishing applications, add more
A. Clipart
B. Font
C. Frames
D. White space
Ans: C
Use Figure 2 to answer questions 40 and 41.
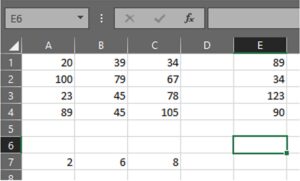
40. Which of the following functions will calculate the products of all the numbers in the worksheet of the spreadsheet application?
A. =PRODUCT(A1:C4,E1:E4,A7:C7)
B. =PRODUCTS(A1:C4,E1:E4,A4:C7)
C. =PRODUCTS(C1:A4)
D. =PRODUCT(A1:E4)
Ans: A
41. Which of the following functions will calculate the average of all the numbers in the worksheet of the spreadsheet application?
A. =AVG(A1:C4,E1:E4,A7:C7)
B. =AVERAGE(A1:C4,E1:E4,A7:C7)
C. =AVERAGE(C4:A1)
D. =SUM(A1:E4/5)
Ans: B
42. The comment function in a spreadsheet application is used to:
I. Take and attach notes to cells
II. Remind the user of complex formulas
II. Provide feedback to others
A. I and II only
B. I and III only
C. II and III only
D. I, II and III
Ans: D
43. Which of the following formulas will display the present calendar month in a spreadsheet application?
A. =TODAY()
B. =MONTH()
C. =MONTH(NOW())
D. =TODAY(MONTH())
Ans: C
44. The value that will be printed at the end of the loop from the following QBASIC code is
LET C = 0
DO WHILE C <= 5
LET C = C + 1
LOOP
PRINT C
A. 1
B. 4
C. 5
D. 6
Ans: D
Check Also: Elective ICT Practicals 2021
45. Which of the following outputs will be displayed when a user executes the QBASIC program below:
READ A
READ B
READ C
READ D
READ E
READ F
LET P=(A*B^2)/2
LET Q=C+D*3
LET R=(E^2+50) + F
DATA 4,5,6,10,8,12
PRINT P, Q, R
END
A. 50 48 162
B. 11 36 126
C. 50 36 126
D. 400 36 48
Ans: C
46. To print the word SCORES beginning with the 24th column, use the QBASIC command
A. PRINT “SCORES”, 14.
B. PRINT (24) “SCORES”.
C. PRINT TAB(24);”SCORES”.
D. PRINT TAB, 24, “SCORES”.
Ans: C
47. Which of the following QBASIC commands demonstrates the correct way of coding the statement “Transfer control to the line labelled ONE if X is between 0 and 12 inclusive”?
A. IF X=12 THEN GOSUB ONE
B. IF X>12 THEN GOSUB ONE
C. IF (X>12 AND X<12) THEN GOSUB ONE
D. IF (X=0 AND X<=12) THEN GOSUB ONE
Ans: D
48. What value will be printed when the following QBASIC code is executed?
LET S=0
FOR C=1 TO 10
LET S=S+C
NEXT C
PRINT S
A. 45
B. 50
C. 55
D. 60
Ans: C
49. The QBASIC code given below has an error. Select the line of instruction in the options provided that will correct this error.
FOR I=1 TO 3
READ N$
PRINT N$
NEXT N
DATA “TOM”, “DICK”, “HARRY”
A. NEXT I
B. PRINT “N$”
C. FOR I$=1 TO 3
D. DATA TOM DICK HARRY
Ans: A
40. The command that is used to detect the presence of a computer on a network is called
A. ipconfig
B. netsh
C. ping
D. telnet
Ans: C
Recommended:
- Elective ICT Pasco 2020 Subjective
- Elective ICT Pasco 2017 Objectives
- Elective ICT Practicals 2018 and Subjectives
- How to use the internet responsibly | Learn with ease on the internet
- How to Pass any Exams with Ease
- Why Students Fail Examination
- Elective ICT trial Questions
- Updates Here: WAEC Finally Releases BECE Time Table 2022 – icreategh.com
Please if you are on any of our WhatsApp platforms, do not join this one.
Join our Discussion Forum below.
<<< CLICK HERE TO JOIN OUR WHATSAPP GROUP >>>
<<< CLICK HERE TO JOIN STUDENTS FORUM ON WHATSAPP >>>
<<< CLICK HERE TO JOIN OUR TEACHERS PORTAL GH ON TELEGRAM >>>
<<< CLICK HERE TO JOIN OUR ICT TEACHERS PLATFORM>>>
Please don’t forget to share this post. Click on the WhatsApp, Facebook, Twitter, Instagram button below to share the post.